Researcher Discovers Tesla Model Y NFC Relay Attack to Unlock and Start Cars

Photo: IOActive
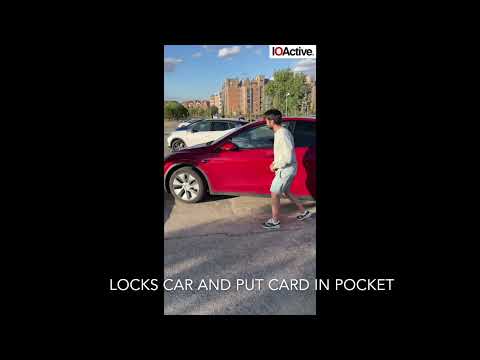
Independent security research firm IOActive has discovered a new relay attack that could allow thieves to unlock and steal a Tesla Model Y, as shown in a video shared on Monday (via The Verge).
IOActive Principal Security Consultant Josep Rodriguez has discovered what he called an NFC relay attack, which requires two people to perform effectively. Additionally, one of the thieves needs to have close proximity to the owner’s key card.
While the person close to the Tesla uses a PRoxmark RDV4.0 device to activate communication with the NFC reader on the driver’s side door pillar, the other person needs to be within two inches of the owner’s keycard.
This allows the Proxmark device to transmit the signal using either Wi-Fi or Bluetooth to the person near the owner, who can then place it near the owner’s key card to transmit authentication back to the person next to the car.
Rodriguez explained that while Wi-Fi and Bluetooth limit the distance between the thieves, the attack is possible from several feet, or even further using devices such as a Raspberry Pi to relay the signals.
Additionally, Rodriguez noted that thieves won’t be able to restart the car once the engine has been shut off.
In January, one teenager from Germany also claimed to have hacked more than 25 Tesla vehicles across 13 countries using a security flaw.
You can watch IOActive’s full breakdown of the NFC Relay Attack on a Model Y below.